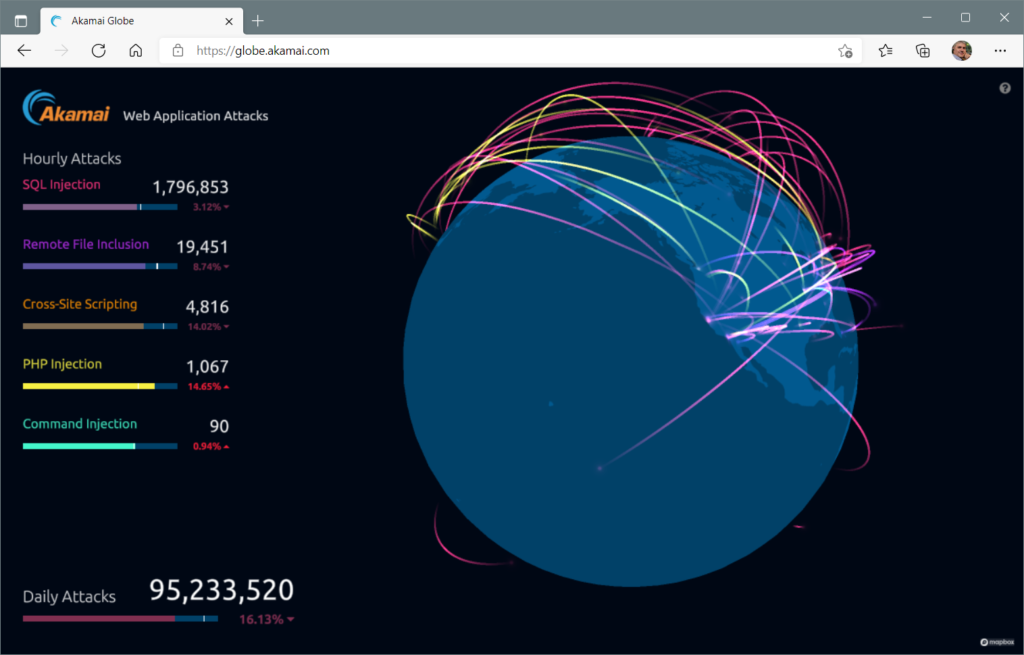
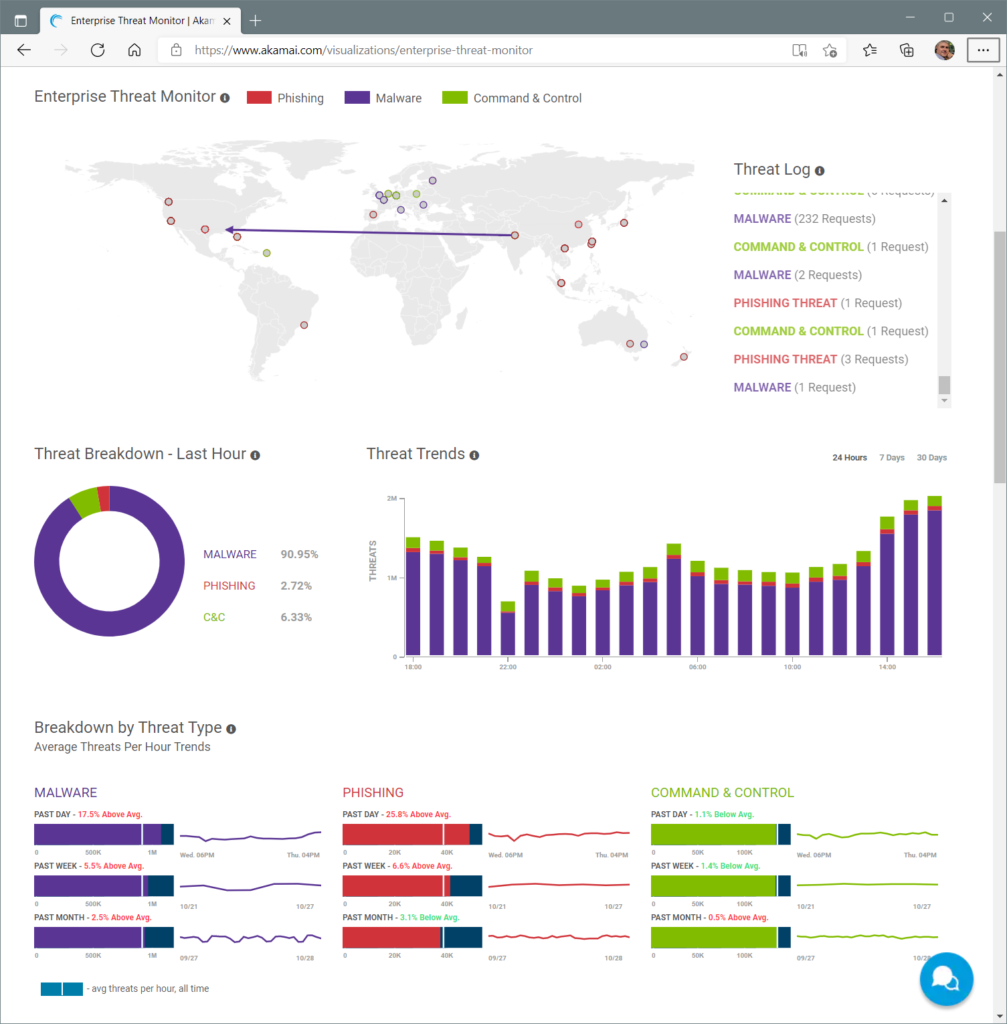
Akamai Technologies, Inc. is a global content delivery network[2] (CDN), cybersecurity, and cloud service company, providing web and Internet security services.[3][4] Akamai’s Intelligent Edge Platform[5] is one of the world’s largest distributed computing platforms. The company operates a network of servers around the world and rents out capacity on these servers to customers who want their websites to work faster by distributing content from locations near the user. When a user navigates to the URL of an Akamai customer, their browser is directed by Akamai’s domain name system[6] to a proximal edge server that can serve the requested content. Akamai’s mapping system[7] assigns each user to a proximal edge server using sophisticated algorithms[8] such as stable matching and consistent hashing, enabling more reliable and faster web downloads. Further, Akamai implements DDoS mitigation and other security services[9] in its edge server platform.
Akamai blog post (external links):
Latest Blog Posts

Securing the Enterprise Network for the Office Anywhere
During the pandemic, it was reassuring to see businesses demonstrating resilience and enabling remote working for their employees — in some cases, practically o…by Octavio Hernandez

Your Best Defense Against Ransomware: Akamai + Guardicore
For decades, Akamai has been focused on solving tough problems for our customers. We started by addressing the challenges of the “World Wide Wait,” and quickly …by Ari Weil

Over 25% of Malicious JavaScript Is Being Obfuscated
Last year, Akamai released research on obfuscation techniques being used by cybercriminals to create malicious JavaScript. The code is unreadable, un-debuggable…by Or Katz

What Microsoft Bing’s IndexNow Means for CDN Users
Microsoft Bing today announced the rollout of IndexNow, a new protocol designed in conjunction with Yandex that can allow “websites to easily notify search engi…by Jon Alexander

Integrating Akamai mPulse with Consent Management Providers
Akamai mPulse is a real user monitoring solution, providing detailed information about the user experiences delivered by your web applications. mPulse can be co…by Simon Hearne

Akamai MFA in Action: Single Sign-On is Phish-Proof and Simple to Use
Breaking news: we just completed an 850-user pilot with Akamai MFA. In this blog, the first in a series, I’ll explain why we switched to Akamai MFA, how we ran …by Keith Tomlinson

Mitigating CVE-2021-41773: Apache HTTP Server Path Traversal
On September 29, Ash Daulton, along with the cPanel Security Team, reported a path traversal and file disclosure vulnerability in Apache HTTP Server 2.4.29 to t…by Assaf Vilmovsky and Maxim Zavodchik

Coming Together to Tackle Phishing — For the Greater Good
Every day, Akamai’s Threat Research team tracks and mitigates phishing attack campaigns to help keep our customers — and their reputations — protected. Recently…by Akamai Threat Research

Attack Campaigns Ramp Up for Organizations Down Under
DDoS and AppSec attacks impacting the ANZ region (Australia and New Zealand) have been in the headlines of late, with several high profile companies seeing prol…by Tom Emmons

Making the Internet Resilient: Part One
Think how many websites you visit or videos you stream. Do you check your bank account or transfer money, download apps, play music, share updates on social med…by Adam Karon

The Impact of Third-Party Scripts on the Facebook Outage
A lot has already been written about the Facebook outage earlier this week. In case you missed it (if that’s possible), Facebook, Facebook Messenger, Instagram,…by Kunjal Botadra

Forrester: Embrace Zero Trust for Australia’s Essential Eight
Elevate maturity levels with a security model that protects your business and enables growth. Featuring research from Forrester: Embrace Zero Trust for Every …by Johnny Yeo










More Stories
Constanta Maritime University
CyBureau
I2DS2